Abstract
It is easy for someone to read data if it is in a plain text, but confidential and sensitive messages in plain text can be easily compromised. Spies use secret codes to communicate with their secret agents. Julius Caesar never trusted his messengers carrying message to his generals. He used to code his message by replacing every A with a D, every B with E, and so on, so only those who knew how to decode this “shift 3” rule could decode the message.
You have full access to this open access chapter, Download chapter PDF
Keywords
These keywords were added by machine and not by the authors. This process is experimental and the keywords may be updated as the learning algorithm improves.
Introduction
It is easy for someone to read data if it is in plain text, and confidential and sensitive messages in plain text can be easily compromised. Information meant for a specific set of eyes must be carefully guarded. Spies use secret codes to communicate with their secret agents. Julius Caesar never trusted his messengers carrying message to his generals. He encrypted his messages by replacing every A with a D, every B with E, and so on, so only the intended recipient could decipher the message.
Information security is the protection of organizational/personal data from unauthorized users. The basic components of Information security are: Confidentiality, Integrity and Authenticity, and Availability. Confidentiality is secrecy. No one else should read the data apart from the one who is sending the data and the authorized receiver. With the increasing use of the Internet as an e-commerce tool, it is important for users, banks, and commercial institutions to make sure that their information is secured and no one is able to read change the data during its transmission.
When computer systems can code plain text and the recipient understands and interprets this coded message, users feel more secure transmitting data over the Internet, or any other media. This method of coding a plain text message into a secret coded message is called cryptography. The method of disguising plain text to hide the actual data is called encryption. The new encrypted text is called ciphertext. The encrypted data is not readable by others and hence it is secur. Once it reaches its destination, the receiver can reverse the process to read the ciphertext. This process is called decryption. The typical process of encryption and decryption is illustrated in Figure 8-1.
Cryptography is the process of converting simple plain text into secret text called ciphertext, and converting ciphertext back to its original simple text, as shown in the Figure 8-1. The process uses algorithms known as crypto-algorithms to perform the encryption and decryption process.
Encryption and decryption are done using a “key” or “code.” Sometimes, only one key is used to perform both encryption and decryption; sometimes two separate keys are used, one for encryption and the other key for decryption.
In today’s Internet world, cryptography applications are used to enable digital signatures, money transfers, online shopping, online booking, and credit card payments, where authentication and privacy are crucial. Cryptography makes transactions on the web more secure through digital certificates, 3-D secure, and other encryption technology.
With the rise in government surveillance of Internet data, which is making headlines every day, people are even more concerned about their privacy and personal data. E-mails sent in plain text can become a serious problem, as someone could tap the network and read your personal e-mail–something that has become quite common. Hence, companies prefer to use encrypted e-mail for employees–certainly, for senior executives at the very least. Though encrypting e-mail may or may not protect an individual or business completely from government surveillance, it can certainly keep your data safe from intruders who are looking to find useful information from your e-mail.
Cryptography is mainly used to protect confidentiality of the data. However, it is not restricted to the confidentiality. It is used for checking integrity and authentication processes as well. For example, in many governance processes, a signature is an essential part of the process for authentication and maintaining integrity. If we make this process computerized, where approval, and other governance is done via network or Internet, then we need a mechanism to authenticate the user’s signature digitally (digital signatures), and provide a digital timestamp. Cryptography provides such a mechanism.
Cryptography is also used to regulate access to your cable or satellite television. It is controlled centrally and only the channels you are subscribed to can be accessed and all other signals are “scrambled” using cryptographic technology. For example, pay-per-view, annual, or monthly subscriptions are all controlled centrally by scrambling and unscrambling signals based on the payment. Setup boxes installed at houses, hotels, and other places will have the ability to decode the channels only upon receipt of payments.
Although cryptography is widely used, its application on the Internet is increasingly demanding and growing as hackers are cracking cryptographic algorithms. Researchers are working on providing better algorithms and keys so that users data and authentication is protected. Cryptography is still fundamentally based on problems that are difficult to solve because of the complexity of the keys for decrypting and encrypting messages or signing documents digitally.
Cryptography, cryptanalysis, and cryptology are interrelated. In general cryptography refers to the technique of encrypting and decrypting plain text. Cryptanalysis refers to analyzing and breaking the keys used for encryption and decryption (generally used by hackers). Cryptology refers to both: study of cryptography and cryptanalysis.
In this chapter, we will focus on the basics of cryptography and its application. We will not be covering in-depth analysis of cryptography itself. There are several textbooks and papers that exclusively discuss different cryptographic algorithms and techniques. Bruce Schneier is known as an authority on cryptography. He has contributed to the community with more than 10 useful books related to the concept of cryptography and has several blogs on the topic.
Cryptographic Algorithms
In cryptography, encryption and decryption are performed using a mathematical function, often known as cryptographic algorithm. The mathematical function consists of keys: a word, number, or phrase. The cryptographic algorithm makes use of one or more of these keys to encrypt the data. The same plaintext can be encrypted using different keys to get different ciphertext. The strength of the encryption depends on the keys and cryptographic algorithm which makes use of these keys to encrypt.
There are three types of cryptoalgorithms (based on key), which are discussed in detail in this chapter:
-
Symmetric Key (Secret Key Cryptography): Uses a single key to encrypt and decrypt the messages
-
Asymmetric Key (Public Key Cryptography): Uses one key to encrypt and another key to decrypt the messages
-
Hash Functions: Uses a mathematical transformation that transforms the message into a fixed length data that is unique to the corresponding source. These transformations are carried out using hashing functions/algorithms and are not normally reversible or are one way hashes.
Figure 8-2 illustrates the above three types of cryptography.
For any encryption approach, there are two major challenges: key distribution and key management. Key distribution is a mechanism to convey the keys to those who need them to establish secure communication. Key management is to manage large number of keys and provide the right key to the right user as needed.
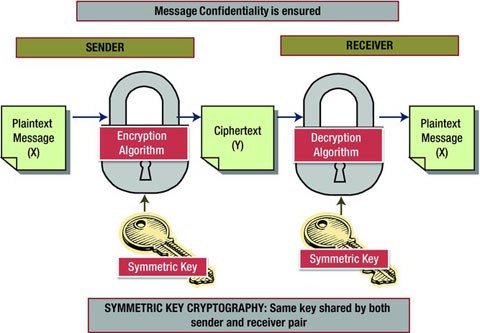
Symmetric Key Cryptography
In this technique a single key is used to encrypt and decrypt the data. Both, the sender and receiver must share the same key in order to share confidential information. Because a single key is used for both encryption and decryption, this method is called symmetric cryptography. In this method, a single key, which is secret, must be known to both the sender and receiver.
Symmetric key cryptography operates in two modes, stream or block. In stream mode, each bit is considered for encryption whereas in block mode, blocks of data are considered for encryption. In case of block mode, one block of data is encrypted using the same key but in case of stream mode, the same block will have multiple key to encrypt the data. Since the messages are normally more than one block, block mode method needs a mechanism to arrange different blocks together.
Figure 8-3 illustrates how the symmetric key cryptography is used to ensure confidentiality of the message that is sent.
There are several algorithms developed for both the modes. The Data Encryption Standard (DES) and the Advanced Encryption Standard (AES) are two block cipher algorithms recognized by US government. DES was developed by IBM as a standard for applications in 1977 and since then it has been used in many applications. DES was the most popular algorithm used across a wide range of applications from ATM encryption to e-mail privacy. 1 However, the known and exploitable weaknesses of DES have caused the community to discourage its use.
In stream mode, encryption is performed one byte at a time. Instead of blocks of data, each byte is encrypted using a stream of keys. RC4 is a variable-key-size stream cipher developed in 1987 by Rivest. RC4 is a stream cipher licensed by RSA which is a widely used stream cypher method.
Some of the most popular cryptoalgorithms are:
-
Data Encryption Standard (DES)
-
Advanced Encryption Standard (AES)
-
Rivest Cipher (RC)
-
International Data Encryption Algorithm (IDEA)
-
Blowfish
DES is one of the first widely used algorithms but it has been cracked and no longer considered secured. AES is used by the US government and IDEA is used by European nations. Blowfish is an open-source symmetric algorithm created in 1993.
Key Distribution
Distribution of the key and managing the key between different set of users is the most challenging task. Symmetric key cryptography is more useful for encryption of files or file systems in the local machines and less useful for communication between the two systems in the network because of “key distribution” challenges.
There are two ways of solving key distribution problems. One approach is to physically exchange the keys in advance. The secret keys are personally handed over to the parties, which is manual. The second approach is to use a “Trusted Key Distribution Center” to distribute the keys, a trusted network entity with whom one has shared the secret key. This process can be automated.
Suppose Anna and Barry want to communicate using a symmetric key. But, they have never met before and thus they do not have the shared keys to exchange information. Now, there are two problems, one is sharing the key but more important is sharing the key with a person who is a stranger but still wants to communicate. A solution that is often adopted is to use a trusted party known as Key Distribution Center (KDC).
The KDC is a server that manages different symmetric keys with each of the registered user. Each user who wants to communicate with the other user must register with KDC. KDC will check the credentials of each user to ascertain the authenticity. A user who wishes to communicate with the other user, let’s say, Anna wants to communicate with Barry, Anna and Barry both have to first register with KDC. Anna takes the first step to send a request for a key as well as the user it wants to communicate. Once the request is processed with proper authentication, KDC sends shared key to both Anna and Barry. Henceforth, both can communicate with each other with the secret key that was given to them by KDC. KDC can also set expiration and other parameters of the key.
Figure 8-4 illustrates the entire process of symmetric key distribution through the KDC.
Asymmetric Key Cryptography
There are two problems with symmetric key cryptography:
-
Distribution of key – Secret key sharing among senders and receivers. If there are n parties involved in the communication then n(n-1) keys to be distributed. Managing this many keys is another problem.
-
Authenticity – Trust and Authenticity of two parties.
In 1976, Diffie and Hellman at Stanford University came up with a new method to solve both the problems of symmetric cryptography that changed the world of cryptography and digital communication radically. This new method is called Public Key Cryptography also known as Asymmetric Key Cryptography.
Public Key Cryptography
Public key cryptography uses a pair of keys for encryption and decryption. A public key is used to encrypt the data and a private key is used to decrypt the data. Using the public key, anyone can encrypt the data, but they cannot decrypt the data. In this approach, both sender and receiver have the ability to generate both keys (using a computer system) together. However, only the public key is made known to the other party, who can download this key even from a web server; the private key is not known to anyone. It is not sent to the other party, hence the problem of distribution of the key never arises. In case of intrusion or any other problems, the system can generate a private key, and a corresponding public key that can be published again. The algorithms that generate keys are related to each other mathematically in such a way that knowledge of one key does not permit anyone to determine the other key easily.
Figure 8-5 illustrates how the confidentiality of a message is ensured through asymmetric key cryptography (alternatively known as public key cryptography).
Figure 8-6 illustrates how the authenticity of the message is ensured through asymmetric key cryptography (i.e., public key cryptography).
Figure 8-7 illustrates how both the message confidentiality and authenticity are ensured through asymmetric key cryptography (i.e., public key cryptography).
The Public Key Cryptography (PKC) concept was invented by Whitefield Diffie and Martin Hellman in 1976 paper. The primary benefit of the PKC is that only the public key is shared, the need to share private key via some secure channel is eliminated, and private keys are not transmitted or shared. A public key system is constructed using a mathematically infeasible solution where one key cannot be generated using the other key and both the keys are required for a secured communication. The historian David Kahn2 described public key cryptography as “the most revolutionary new concept in the field since polyalphabetic substitution emerged in the Renaissance.”
There are many algorithms based on PKC, but the most popular ones are:
-
Diffie Hellman
-
RSA (Rivest, Shamir, Adleman)
-
Digital Signature Algorithm (David Kravitz)
RSA Algorithm
RSA is an encryption and authentication algorithm developed by Ron Rivest, Adi Shamir, and Leonard Adleman. It is used in many applications including browsers. The algorithm is owned and licensed by RSA Security which is part of EMC2. It uses one key for encryption and another key for decryption. The mathematical function for generating keys itself can be found in specifications and standards as well as in the RSA web page. Using the mathematical functions, two sets of numbers (keys) are generated: public key and private key. Both the public key and private keys are required for encryption and decryption but private keys are kept private by the owner and are never sent across the Internet. The public key is used to encrypt the data and private key is used to decrypt when the message confidentiality has to be maintained.
Authentication can be provided by using the PKC system and RSA algorithm (RFC 3447). The message is encrypted using the private key of the sender to authenticate the sender. As the sender’s private key is only held by the sender, encryption by using the private key by the sender authenticates that the message was in fact originated by the sender himself. During the authentication process, a private key is used by the sender and the receiver decrypts using the public key. This does not guarantee confidentiality, but does assure the authenticity of the message. When the original message is transformed using the message digest function and encrypted by the private key, it is known as a digital signature. It is also possible to encrypt a portion of the message being sent using the private key of the sender to demonstrate the authenticity rather than encrypting the entire message. Such a system should have the capability that the unencrypted portion is not possible to be modified without the modification of the encrypted portion.
Table 8-1 summarizes the entire authentication process.
The RSA keys are derived from a variable size encryption block and a variable size key. The key-pair (public and private) is derived from a very large prime number, chosen according to special rules. The strength of RSA depends on the key length but choosing a long key can slow down the system. For bulk data encryption, it is recommended to use DES for better performance.
If you want both the confidentiality and the authenticity of the message, the following encryption mechanism has to be used:
-
The message has to be first encrypted using the private key of the sender.
-
The encrypted message is then encrypted using the public key of the receiver.
-
The encrypted message is sent to the receiver.
-
The receiver on receiving the encrypted message decrypts it using his (receiver’s) private key.
-
The semi-decrypted message is then decrypted using the public key of the sender.
-
The receiver obtains the plain text message.
Advantages of Public Key Cryptography
The advantages of public key cryptography are:
-
No need to exchange the keys
-
Another key cannot be derived from one key
-
The confidentiality of the message can be ensured by using the public key cryptography
-
It is possible to establish authentication of the sender by using public key cryptography (digital signature)
-
It is possible to ensure the confidentiality and authentication of the message at the same time
-
It is possible to use public key cryptography for session key exchange
Applications of PKC
Public Key Cryptography is used in a number of applications and systems software. Some examples of application of cryptography are:
-
Digitally signed document
-
E-mail encryption software such as PGP and MIME
-
RFC 3161 authenticated timestamps
-
Digital signatures in the Operating System software such as Ubuntu, Red Hat Linux packages distribution
-
SSL protocol
-
SSH protocol
Public Key Infrastructure (PKI)
A Public Key Infrastructure (PKI) enables users to securely transact through the use of public key cryptography. Key pairs are obtained from a third-party trusted authority called Certificate Authority (CA). The PKI provides an infrastructure to issue a “digital certificate” that identifies an individual or organization. Based on the identity of the digital certificate, transactions are made securely over public networks such as the Internet. The PKI is based on the use of public key cryptography, which is commonly used.
A public key infrastructure consists of:
-
A Certificate Authority (CA) that issues and verifies digital certificates. A certificate includes the public key or information about public key
-
A registration Authority (RA) which verifies the user’s authenticity for CA before CA issues a digital certificate
-
A secured storage place to hold the certificates and public keys
-
A certificate management system
-
Hardware, software, policies, procedures, and people used to create, manage, and revoke digital certificates along with the distribution and storage of the digital certificates
A certificate contains information referring to a public key, issued by a Certification Authority (CA). The information in the certificate should conform to the ITU (IETF) standard X.509 v3. Certificates conforming to that standard include information about the published identity of the owner of the corresponding public key, the key length, the algorithm used, associated hashing algorithm, dates of validity of the certificate, and the actions the key can be used for.
Certificate Authority (CA)
A CA is responsible for issuing certificates. CA issues the digital certificate based on the recommendation of RA. This digital certificate is signed by the CA using its own private key. The CA issues the certificate which contains the public key of the party who owns the certificate. Certificates have to be purchased from the CA. CA can issue a certificate only after it confirms all the credentials to prove your identity. Once identity is proved, it stamps the certificate to prevent modifications of the details contained in the certificate. CA is analogous to a passport agency. An individual or organization may have any number of certificates issued by different CAs. Different web applications may insist to use a particular certificate. For example, a particular bank may insist to use a certificate issued by that bank for a secured transaction, whereas some other web site may accept any certificate issued by any CA.
Registration Authority (RA) is a third-party verification agency for a Certificate Authority (CA), to perform the verification of the organization or individuals who have applied for the certificate. Final component of the PKI is the Certificate Management System (CMS) through which certificates are published, renewed, or revoked. Examples of Certificate Authority (CA) include Verisign, Thawte, SSL.com, RapidSSL, Network Solutions, GlobalSign, Digicert, Enutrust.net, PinkRoccade, and PKI.CAcert. 24
Digital Certificate
Digital Certificate provides an electronic identity to conduct secure transactions by providing your identity (authentication). It is similar to a passport or driver’s license. With a digital certificate, an organization or an individual can provide authentication for all the transactions with friends, business partners, and other online services. Digital certificate assures identity among all the parties involved in the transactions. The most widely used format of a digital certificate is as defined by the CCITT X.509 standards. 25 Digital certificate uses public key cryptography to verify the integrity of the certificate itself.
Hash Function Cryptography
Hash functions, also called message digests, use a fixed length hash value to transform the data that makes it difficult for someone to decrypt or change the data without affecting the hash value, thus securing the data from intruders. Hashing functions are one-way mathematical functions that are easy to compute but hard to reverse. A hash function H( ), applied on input (x), and returns a fixed string, hs. Mathematically it is written as hs = H(x). A cryptographic hash function in general should have the following properties:
-
Flexible input length (x)
-
H(x) should be relatively easy to compute
-
H(x) is one way function and cannot be reversible
-
The output is of fixed length and does not depend on input length
Hashing is generally used in the following situations:
-
Password management in case of PPP, CHAP, and Microsoft EAP. This method of cryptography is normally used in operating systems to protect passwords.
-
Digital signatures and file integrity checkers to check the integrity of data.
Hashing functions are used to vouch for the integrity of the message by appending the message with the hash value. If the message is changed, the hash value when recomputed will not match the precomputed hash value. In order to avoid man-in-the middle attacks, it is ideal to send the hash value in a secure way to the intended party. Such secure transfer is possible using public key cryptography.
Further, hash value is used to store passwords of the operating systems like Microsoft Windows. Here, the original passwords are not stored; instead the SAM corresponding hash values are stored. These provide high security to the passwords, as hash value is not reversible to find out the original password. Only when the passwords are entered in the system will it compute the hash value and check with the hash value stored in the SAM.
“Salting” the password before hashing by either suffixing or prefixing it with a random string decreases the possibility of cracking the password.
Hashing is also used in some of the implementation of digital signatures which vouches for the integrity of the message sent. Hashing functions are also used in virus detection as well as intrusion detection.
Figure 10-8 illustrates how hashing ensures the integrity of the message that is sent.
Popular Hashes
MD5 (Message Digest Function 5), SHA1 (Secure Hash Algorithm 1), SHA2 (Secure Hash Algorithm 2), and SHA3 (Secure Hash Algorithm 3) are the popular hashing functions /algorithms. MD5 outputs are of 128 bits and are popularly used for storing of the passwords as well as to ensure file integrity. MD5 is prone for collision.
SHA algorithms again provide for one way hash. SHA1 provides for 160 bit output. SHA-224, SHA-256, SHA-384, and SHA-512 are known as SHA-2. SHA3 is the most advanced hashing function which was announced by NIST in 2012. SHA-3 has a unique structure known as sponge construction.
MAC (Message Authentication Code) is another popular hash function which is also known as a Keyed Hash Function.
Digital Signatures
A digital signature is like a handwritten signature but it is in the digital form for an electronic document. The document containing the digital signature is verified by the recipient using a hash function to check whether the message has been altered either intentionally or accidentally during the transmission. If the message is altered, the hash function returns a different result. Digital signature ensures authenticity and non-repudiation.
Here, usually the hash value is encrypted with the sender’s private key. This provides for the authenticity. When the receiver decrypts the private key using the sender’s public key, he gets the hash value. He can check this hash value with the hash value generated using the hash algorithm from the message received. Alternatively, both the message and the appended hash value both can be encrypted with the sender’s private key in a similar way as above. If both the hash value received and the hash value generated from the message received tally that means the integrity of the message is maintained. Because it has been signed by the sender’s private key, the message sender is also authenticated. Another alternative is to encrypt the message and the hash value using the symmetric key shared between both the parties.
Summary of Cryptography Standard Algorithms
Table 8-2 summarizes some of the Symmetric cryptographic algorithms that are used today.
Table 8-3 summarizes the Public-Key Cryptography Algorithms that are commonly used today.
Table 8-4 summarizes some of the Hash function algorithms that are commonly used.
Each of the algorithms in Table 8-4 is used in different applications and for different purposes. For example, Hash function algorithms are well suited for data integrity. Any change made to the content during the transmission will result in a hash value different from the original value sent by the sender. Since it is highly unlikely that the same hash value is generated for two different messages, data integrity is ensured.
Symmetric key cryptography is suited for encrypting and decrypting messages, thus providing privacy and confidentiality. The sender can generate a key for each data session to encrypt the message and the receiver can decrypt the message but needs to have the same key for the same session. Symmetric key cryptography also may be used for file encryptions.
Public Key cryptography technique uses a pair of keys called private and public. This is used for not only confidentiality of message but also for non-repudiation and user authentication.
Table 8-4 provided an overview of different algorithms used for different types of cryptography techniques. Table 8-5 provides an overview of some of the common cryptographic algorithms that are used in various applications, particularly in e-commerce applications.
Disk / Drive Encryption
With the increased use of the mobile devices like laptops and the storage of confidential data on their hard disk and data carried on USB and other drives, we need to protect the data from theft and misuse. Hence, the disk encryption utilities have emerged. The entire hard disk, USB drive, and other drives can be encrypted so that the data on them cannot be read and misused by unauthorized persons. Now, we have the possibility to burn the data on to portable disks but encrypt them so that unauthorized persons will not be able to misuse them.
The utilities and tools such as TrueCrypt and Gilisoft are widely used for disk encryption, and are found to be very effective in disk encryption. There are many other tools available such as DriveCrypt, DiskCryptor, Rohos Disk Encryption, and Symantec Drive Encryption.
Attacks on Cryptography
There are various attacks possible on cryptography. Some of the common attacks are:
-
Rubber Hose Attack: Obtaining by force the secret key like password to the file from those who have them
-
Ciphertext-only Attack: Here the attacker has the ciphertext and tries to get the encryption key using the ciphertext
-
Known-plaintext Attack: Here the attacker has some plaintext. Using this he tries to get the encryption key
-
Chosen-plaintext Attack: Here the attacker uses his own plaintext. He then encrypts them and analyses the resulting output, i.e., ciphertext.
-
Adaptive Chosen-plaintext Attack: Here the attacker uses various plaintexts. The subsequent plaintext will be used by him based on the result of earlier output.
Brute force and Frequency Analysis methods are popularly used by the attackers to break the encryption key.
Chapter Summary
-
We discussed encoding of messages to ensure the secrecy of the message being sent. We also explored encryption, decryption, cryptography, cryptanalysis, and cryptology. We discussed how cryptography helps in maintaining the confidentiality of the message as well as assures the authentication of the message.
-
We explored various cryptographic algorithms such as symmetric key cryptography and asymmetric key cryptography. We also explored the problem of key distribution in the case of symmetric key cryptography and how this can be resolved using the third party. We then explored the asymmetric key cryptography and under that looked into the public key cryptography and how it resolves the issue of key distribution. We looked into the concepts of private key and public key. We also elaborated further as to how this helps out in ensuring the confidentiality of the messages being sent as well as the authentication of the messages. We briefly touched upon the RSA algorithm. We then briefly touched upon the applications and advantages of the public key cryptography. We also briefly touched upon Public Key Infrastructure, the role of Certificate Authority, and Digital Certificates.
-
We briefly discussed hashing algorithms, some of the popular hashing functions/algorithms, and the uses of hashing functions/algorithms. We also briefly described how Digital Signatures are implemented using hashing algorithms.
-
We listed various symmetric, asymmetric, and hashing algorithms along with further references to them.
-
We looked into the disk encryption mechanism to protect the drives / disks from misuse and then concluded the section with the possible attacks on cryptography.
Author information
Authors and Affiliations
Rights and permissions
Open Access This chapter is licensed under the terms of the Creative Commons Attribution-NonCommercial-NoDerivatives 4.0 International License (http://creativecommons.org/licenses/by-nc-nd/4.0/), which permits any noncommercial use, sharing, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence and indicate if you modified the licensed material. You do not have permission under this licence to share adapted material derived from this chapter or parts of it.
The images or other third party material in this chapter are included in the chapter’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the chapter’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder.
Copyright information
© 2014 Umesh Hodeghatta Rao
About this chapter
Cite this chapter
Rao, U.H., Nayak, U. (2014). Cryptography. In: The InfoSec Handbook. Apress, Berkeley, CA. https://doi.org/10.1007/978-1-4302-6383-8_8
Download citation
DOI: https://doi.org/10.1007/978-1-4302-6383-8_8
Published:
Publisher Name: Apress, Berkeley, CA
Print ISBN: 978-1-4302-6382-1
Online ISBN: 978-1-4302-6383-8
eBook Packages: Professional and Applied ComputingApress Access BooksProfessional and Applied Computing (R0)